The Hazard You Hope Never Happens: Being Hacked. Here’s How To Avoid It

A CNNMoney analysis in May of this year reported that about half of all American adults’ personal information was compromised in the last twelve months due to data breaches at large companies and organizations. In August of 2014 alone, we’ve seen three more hacking victims; Community Health System, UPS, and J.P. Morgan. These ongoing events worry many people. To help you better protect yourself from being hacked personally, here are some things you should do when using the internet.
- Always install anti-virus software on your computer. I recommend using a paid version instead of a free one. This investment is a fraction of the cost and time of having to clean your infected computer. Generally, free versions have less-frequent malware-signature updates than the paid versions do, which can open a window of opportunity for cyber criminals to hack you.
Also, a paid version means you won’t have to deal with the constant and annoying pop-up offers for upgrades. There are number of quality anti-virus software options to choose from: Avast, AVG, Kaspersky, McAfee, Norton, Trend Micro, VIPRE, etc. - Be extra careful where you click, especially when you’re directed to new websites or emails that look suspicious. If a link looks suspicious, don’t click on it; exit the site or delete that email right away. If an email looks a little suspicious but you think it may be a customer contacting you, then, without clicking on the link, just rest your mouse cursor on the link to see what url the link is connected to.
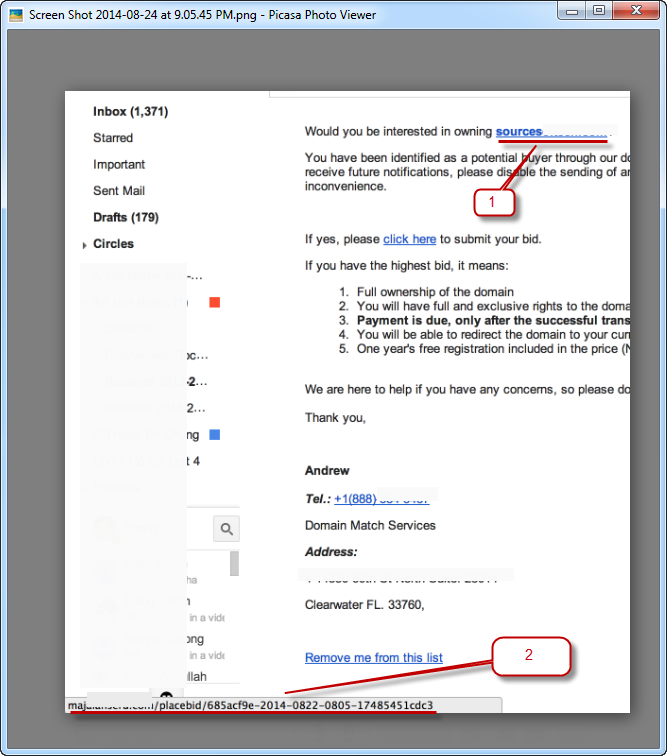
When hovering over the link, you should see the url show on the left bottom corner of your web browser (see image #1). If the content of the email is about a customer name “John Doe” from B2Bconstruction.com company, but your mouse hover shows the url to be “XvXhotck.net,” then that is most likely a phishing email. You should delete that email right away. A “phishing email” is an email that contains content masquerading as a trustworthy entity in an attempt to acquire sensitive information from you. What happens is, when you click on the link, it re-directs you to websites that are infected with malware or spyware. - Don’t download from unknown sources that are not yet verified, no matter how attractive or interesting the sources look. This is an old trick many cyber criminals still use to hook you. Also, if you see a download offer that looks too good to be true on the web, then it is.
- Don’t use one password for all of your online accounts and don’t set your browser to remember your password to automatically log you in. Create different passwords for each of your online accounts. You can use password-generating software like “One-pass” at https://agilebits.com/onepassword or “Kee-pass” at http://keepass.info/ to generate random passwords with 36+ characters. For example: Fg^&3naf8e*#N#LF23&h=diIHObbHLS35y6K. Don’t worry; you don’t have to memorize all of those passwords. That software will store them for you in a “password vault” on your computer. You only need to remember one Master Password in order to access your password vault. This software often offers both free and paid versions.
- Don’t use your pet names or names of your family members or dates of birth as passwords. Cyber criminals can easily access your social media pages and other informational pages to get that information about you. It is best to use the password generator software mentioned above or you can manually generate 36+ character passwords that have symbols, numbers, upper case and lower case letters in them.
- Change your passwords every 3-5 months. If you use a password generator software as suggested above, you still need to change your passwords every 7-9 months. For your Master Password, try to keep it in a secure place and don’t change it very often. This is because changing your Master Password often will increase the chances you’ll forget it. If you forget your Master Password, you will not be able to open your password vault to retrieve other passwords.
- Keep all your web browsers up-to-date. If you are using Internet Explorer (IE), Firefox, etc. – You should periodically (every 3-5 months) check for new browser updates by Google search for keywords such as: IE browser update, Firefox browser update, etc. If there is a new browser update for your web browser, you should update it right away. One extra effort: You should also clear your browser’s cache regularly to remove temporary files that were stored on your memory or hard disk.
- Use 2-step authentication to login to your Gmail, Yahoo mail, Hotmail accounts. This will help protect your accounts from email hijackers. Why should you do this? If your email account is hijacked, that person will have all the email addresses of the people you have been in contact with, including your friends, family members, colleagues and even boss. The hijacker can pose as you to send other people phishing emails to hack their computers. Imagine how upset those people would be if they discover that their computer got hacked because of a link that was sent from your email.
-
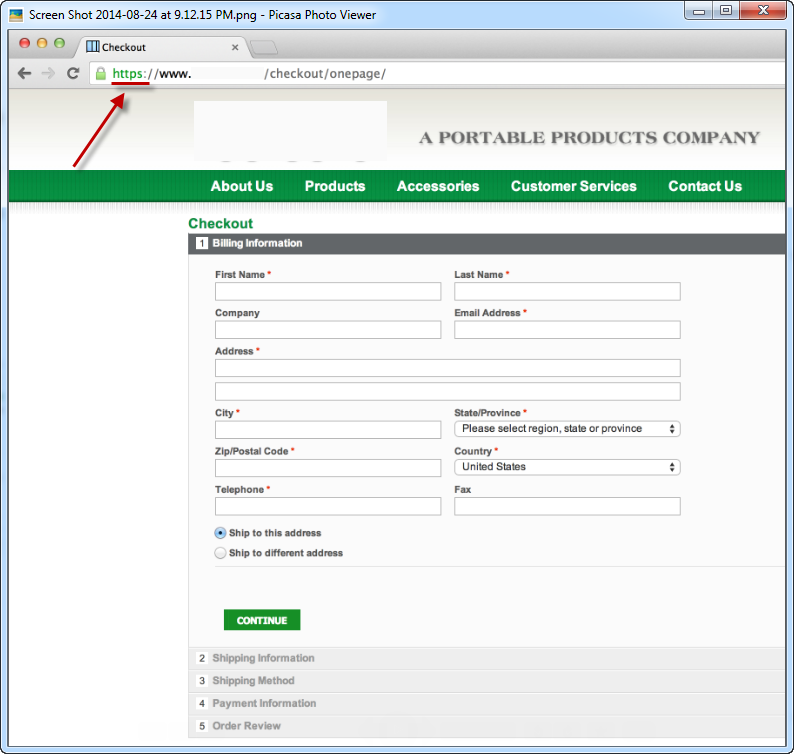
9 Critical Factors In E-Commerce Website Design and Usability If you are about to purchase online, make sure at the “Check Out” page that the beginning of the site’s url is “https:” If that page only has “http:” then don’t buy on that page. “https:” means that the site has secured an SSL certificate to protect buyers’ confidential information on that page (see image #2).
- Be careful who you “friend” on Facebook and other social media pages. Cyber criminals might try to get in your group of friends on Facebook to post links on your social page, which if clicked on will direct your real friends to spam sites.
- Don’t access your confidential accounts while using a free public WiFi network. Confidential accounts include things like your bank, the IRS, your student loan company website, etc. This opens the door to hackers accessing your private information. Cyber criminals know where the free WiFi networks are, and they take advantage of free WiFi networks at places like coffee shops or public libraries.
When you connect to the WiFi of a coffee shop or library, you really don’t know whether their network has been compromised or not. So do not login to your confidential accounts while you are on a public network. If you have a smartphone, you can use your smartphone as a WiFi hotspot to provide an internet connection to your laptop or tablet. But make sure your password to your smartphone’s WiFi hotspot is strong one, one that is very hard to guess. - Last, but most importantly, you need to check your home internet router to make sure its current password is very hard to guess. You don’t want your internet connection to be tapped into easily by outsiders. If you follow the other steps above correctly but fail to use a strong password when you configure your home router, you’ll still be vulnerable to cyber attacks at home.
Following these twelve tips will help you protect yourself and others from cyber criminals. Hopefully, companies and organizations will learn from this hacking phenomenon and invest more into their security systems to better protect consumers moving forward. If you find this article helpful, please share it with your family and friends. Thank you!
By ProWeb365: Internet Marketing Company